Industrial / Reseach Projects
Beyond the mentioned projects below I am also involved in confidential projects.
Cross-Location Project
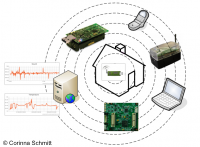
Secure and Efficient Wireless Sensor Network (SecureWSN)
- Project duration: April 1, 2013 - ongoing
- Funding scheme: Personal and internal research project started at the Technische Universität München (TUM), continued at the University of Zurich (UZH), and now continues at the Research Institute CODE
- Project description: SecureWSN is an IoT Framework supporting constrained IoT platforms like sensor devices from different vendors. SecureWSN offers different security algorithms for efficient and secure communication within the sensor networks to the sink. The sink is a framework called CoMaDa offering users configuration, management and data handling functionality for deployed network. Further a mobile framework is included in SecureWSN offering the user to give authorized access to collected data of deployed network and allows authorized users to query immediate data collection (e.g., in emergency cases or in absence from home).
- More details: SecureWSN Project Page
@ Research Institute CODE, University of Federal Armed Forces Munich (UniBw M), Germany

Adapting Cyber Awareness for Evolving Computing Environments (NEWSROOM)
- Project duration: December 1, 2023 - November 30, 2026
- Funding scheme: European Defence Fond, EDF-2022-RA, No. 101121403
- Project description: Cyberspace has become an increasingly contested military domain. To mitigate significant incidents with immediate consequences for both military and civil critical infrastructures, strategic cooperation among EU member states and allied countries in cyber defence is needed. The first step towards effective defence is to obtain situational awareness, which is the basis for any successful counteraction. In particular, cyber situational awareness (CSA) aims at providing all stakeholders and personnel of all levels and forces in the chain of command with accurate information about the current threat landscape, according to the individual needs of the users.
Building a CSA, especially in a cross-domain and cross-country fashion, is a complex task, requiring successful integration of research from different fields, including but not limited to data and CTI collection, collaborative and federated learning, attack behaviour classification, visualisation techniques, cryptogaphy for CTI sharing and trust, or deception technologies and digital twins. However, state of the art solutions do not provide a full integration of all necessary technologies and tools to offer a holistic CSA picture.
The main ambition of NEWSROOM is therefore to overcome the current limitations, by studying all relevant CSA aspects, and designing an integrated CSA platform combining data insights, collaborative intrusion detection for attack classification, and information and CTI sharing considering military standards regarding information security and confidentiality. Advanced visualisation concepts will allow for a mission-specific view at all levels of the command hierarchy. Following a co-creation approach involving all relevant stakeholders, NEWSROOM will identify relevant application scenarios for CSA technoligies in cyber defence, which will be validated in cyber range environments to enable realistic conditions for testing CSA solutions and processes, and training military staff. - Consortium details: 4 Universities and 13 Industry Partners

Capacity Building for the German National Coordination Centre for cybersecurity in industry, technology and research (NCC-DE)
- Project duration: October 1, 2023 - October 31, 2025
- Funding scheme: EU-Digital Europe Programme (DIGITAL), No. 101126787
- Project description: The European Parliament and the European Council have agreed to establish the European Cybersecurity Competence Centre (ECCC), and a network of national coordination centres extending across the European Union on basis of the EU regulation 2021/887. The ECCC and the network are intended to pool investment in cybersecurity research, technology and industrial development and to better coordinate planning the Horizon Europe and Digital Europe programmes. Germany's National Coordination Centre (NCC-DE) for cybersecurity in industry, technology and research is a joint effort by the Federal Ministry for Economic Affairs and Climate Action (BMWK); the Federal Ministry of the Interior and Community (BMI); the Federal Ministry of Defence (BMVg) and the Federal Ministry of Education and Research (BMBF), as well as individual ministries executive agencies (the Federal Office for Information Security (BSI), the Research Institute CODE (RI CODE) and the DLR Projektträger). The BSI serves as the single point of contact for the ECCC, the NCC-network and the national stakeholders. The NCC-network will intensify exchange among the member states, enabling interested parties in government, industry and the research community in the EU to identify partners for multilateral projects more quickly and easily, thereby increasing the EU's digital sovereignty. Within each member state, the respective NCC promotes and intensifies dialogue and exchange among interested national partners. In this way, the flow of information to the ECCC will be consolidated to provide optimal support to the national cybersecurity community and to ensure that national interests are represented effectively in the EU's funding process. The funding from the Digital Europe Programme is to be used to support the initial establishment of the NCC-DE, which has already been set up and is to remain active beyond the funding period. The funding is intended to ensure that basic tasks are implemented quickly and effectively.
- Consortium details: 1 Universities and 2 Industry Partners
Air Mobility Integration U-Space (AMIUS)
- Project duration: January 1, 2022 - December 31, 2024
- Funding scheme: Bavarian Aerospace Program, No. ROB-2-3410.20-04-11-15/HAMI-2109-0015
- Project description: The overall objective of the AMI-AMIUS joint project is to create the first integrated Bavarian U-space connecting the city of Ingolstadt with Manching Airport. In addition to the activities described here, this U-space is available as a real test field for use by Bavarian companies in the eVTOL and unmanned aerial systems (UAS) industry. The project investigates how a U-space based on digital services can integrate today's air traffic, including its processes and technologies, with future deployment scenarios of UAS and eVTOLs in a common airspace. For this purpose, the required air traffic management functionalities for safe, integrated and efficient operations, will be provided and demonstrated by the U-space services defined by the European Union Aviation Safety Agency (EASA). Based on these digital services, flights within the Manching control zone, for example from the Drone Center to Ingolstadt main station, are planned as concrete use cases. These practical demonstrations will be supported by corresponding scientific model-based preliminary investigations, multimodal simulations with different traffic systems, feasibility studies as well as cost analyses by the participating universities. To guarantee safe and efficient integrated operations of UAS, eVTOLS and general aviation in the future, novel traffic concepts are required. For this purpose, the existing airspace management must be supplemented by an integrated UAS Traffic Management System (UTM) and thus expanded by the dimension of the previously uncontrolled airspace. The focus is on the design and technical implementation of the demonstrator using a UTM system and appropriate ground infrastructures, complemented by innovative communication technologies and a central control station. The project will also investigate how the data flow between the participating airspace users and the storage of relevant data can be secured by various measures against unauthorized external interference.
One of the academic partners - the UniBwM - has a bilateral cooperation established with the Institute of Air Transport Systems (ILT) at the Technische Universität Hamburg (TUHH), Germany. This alliance will pursue two goals in the field of UAS: (1) On the basis of a scalable model-based approach in close connection with real-world test approaches of the project partners, robust statements are to be made on the realization of the necessary command and control and communication infrastructure for urban air mobility. (2) Solutions for secure cloud-based data storage during operation and over the life cycle will be elicited to reduce the delay of data analysis and data communication. - Consortium details: 2 Universities (+ 1 bilateral cooperation) and 6 Industry Partners

Cyber security cOmpeteNCe fOr Research anD InnovAtion
- Project duration: January 1, 2019 - December 31, 2022
- Funding scheme: EU Horizon 2020, H2020-SU-ICT-03-2018, No. 830927
- Project description: The aim of the project is the networking of cyber security centers in Europe, the development of IT products and services with industry and the establishment of a platform for the training and further education of IT competences throughout Europe. The consortium aims to protect Europe and the digital society against cyber attacks by developing concepts, tools and products. This protection covers the entire span of society. From the citizens, over enterprises, up to national institutions and mechanisms.
- Consortium details: 17 Universities, 3 Research Institutes, and 23 Industry Partners
BMBF-Verbund-Forschungsvorhaben BERKoS
- Project duration: April 1, 2017 - February 28, 2021 (member since June 2018)
- Funding scheme: Bundesministerium für Bildung und Forschung (BMBF) / VDI, No. 13N14431
- Project description: Establishment of a knowledge community platform with the aim of supporting German applicants in obtaining European funding in the field of general security research. BERKoS is part of the project fit4sec, which is funded by the Federal Ministry of Education and Research (BMBF) as part of the measure "German applicants fit for Europe". From 2013 to 2016, fit4sec initially supported German companies in forming consortia for the EU Research Framework Programme Horizon 2020 in the area of "Secure Societies". In 2017, the project team grew by three central end-user partners as part of the "lighthouse project" in order to provide targeted support in meeting the challenges of increased user orientation in European security research.
- Consortium details: 1 University, 1 Research Institute, and 4 Industry Partners
@ Cooperative Systems (COSY) Group, University of Vienna, Austria

Symbiosis of Smart Objects Across IoT Environments
- Project duration: January 1, 2016 - December 31, 2018 (consultant Jul.-Dec. 2016 and Mar.-Aug. 2017)
- Funding scheme: EU Horizon 2020, H2020-ICT-2015, No. 688156
- Project description: symbIoTe comes to remedy the fragmented IoT environment by providing an abstraction layer for a "unified view" on various platforms and their resources so that platform resources are transparent to application designers and developers. In addition, symbIoTe also chooses a challenging task to implement IoT platform federations so that they can securely interoperate, collaborate and share resources for the mutual benefit, and what is more, support the migration of smart objects between various IoT domains and platforms, i.e., "smart object roaming". symbIoTe will achieve all of the above by designing and implementing an Open Source mediation prototype.
- Consortium details: 4 Universities, 4 Research Institutes, and 8 Industry Partners
@ Communication Systems Group, Department of Informatics, University of Zurich, Switzerland
Management of the Future Internet (FLAMINGO)
- Project duration: November 1, 2012 - December 31, 2016 (member since April 2013)
- Funding scheme: EU NoE, No. FP7-ICT-2011-8-318488
- Project description: The goals of FLAMINGO are (a) to strongly integrate the research of leading European research groups in the area of network and service management, (b) to strengthen the European and worldwide research in this area, and (c) to bridge the gap between scientific research and industrial application. To achieve these goals, FLAMINGO performs a broad range of activities, such as to develop open source software, establish joint labs, exchange researchers, jointly supervise Ph.D. students, develop educational and training material, interact with academia and industry, organize event, and strongly contribute to (IETF and IRTF) standardization.
- Consortium details: 6 Universities, 1 Research Institute, and 1 Industry Partner
Socially-aware Management of New Overlay Application Traffic combined with Energy Efficiency in the Internet (SmartenIT)
- Project duration: November 1, 2012 - October 31, 2015 (member since April 2013)
- Funding scheme: EU FP7, No. FP7-ICT-2011-8-317846
- Project description: The tighter integration of network management, overlay service functionality, and overlay application knowledge, as for instance of Online Social Networks and Quality-of-Experience metrics, can lead to cross-layer optimization of network operations. Therefore, SmartenIT considers this as the promising approach to offer a new business potential in operational perspectives for all stakeholders involved, including cloud providers, Internet Service Providers, telecommunication providers, overlay providers, and application providers. By addressing accordingly load and traffic patterns of the Internet traffic or special application requirements and by exploiting them at the same time with respect to social awareness (in terms of user relations and interests), QoE-awareness, and energy efficiency with respect to both end-user devices and underlying networking infrastructure, SmartenIT is dedicated to ensure an operationally efficient management of traffic, exemplified with real-life scenarios.
- Consortium details: 5 Universities, 1 Research Institute, and 4 Industry Partner
Object Tracking in the Internet of Things (OTIoT)
- Project duration: January 1, 2017 - May 31, 2018
- Funding scheme: self-funding
- Project description: The key challenges for this research are to develop a secure solution for tracking different objects indoor and outdoor having unique IDs, support ID and privilege management to control access and enhance object tracking (e.g., due to filtering), and a user-friendly graphical user interface (GUI) - the OTIoT App - scaling for different devices (e.g., smartphone, tablet, PC). Outcomes of OTIoT will result in a Swiss-made, highly flexible eService framework allowing to track objects (indoor and outdoor) respecting personal requirements and legal aspects in parallel, as well as new communication technologies (e.g., LoRa) and trust-building solutions (e.g., blockchains) for an anti-theft and protection system.

Symbiosis of Smart Objects Across IoT Environments (symbIoTe)
- Project duration: January 1, 2016 - December 31, 2018 (since Sep. 2017 full consoritium partner)
- Funding scheme: EU Horizon 2020, H2020-ICT-2015, No. 688156
- Project description: symbIoTe comes to remedy the fragmented IoT environment by providing an abstraction layer for a "unified view" on various platforms and their resources so that platform resources are transparent to application designers and developers. In addition, symbIoTe also chooses a challenging task to implement IoT platform federations so that they can securely interoperate, collaborate and share resources for the mutual benefit, and what is more, support the migration of smart objects between various IoT domains and platforms, i.e., "smart object roaming". symbIoTe will achieve all of the above by designing and implementing an Open Source mediation prototype.
- Consortium details: 4 Universities, 4 Research Institutes, and 8 Industry Partners
@ Chair for Network Architectures and Services, Department of Computer Science, Technische Universität München, Germany

Autonomic Home Networking (AutHoNe)
- Project duration: January 1, 2008 - December 31, 2010 (member since April 2008)
- Funding scheme: EUREKA-Verbundsprojekt, Teilvorhaben: Autonome Sichere Netzwerke, No.CELTIC CP3-001
- Project description: The main objective of AutHoNe is to design an innovative home network communication architecture allowing self-management, configuration and maintenance required for future application scenarios. Key issues are concepts for trust and security and the integration of wireless sensor networking technologies.
- Consortium details: 1 University, 1 Research Institute, and 2 Industry Partner
Security in Generic Identity Management (IDM) Systems
- Project duration: April 1, 2008 - December 31, 2008
- Funding scheme: Commissioned research
- Project description: The project consists of two work packages (WP2 and WP3), which are each associated with corresponding tasks of the NSN internal project on Generic IDM. In WP2 use cases and requirements for Telco as Identity Provider (IdP) was specified. This work package will provide support for describing and assessing selected use cases for Telco as Identity Provider (IdP), and for IdP-based applications with special focus on Use Case 3 (User Account Provisioning), alternatively on Use Case 1 (Web Single Sign On with existing user account over 3GPP Access Network). WP3 designs and engineers the security and privacy features of the innovative IdP to be operated by Telcos, both for its overall architecture and for its sub-systems, based both on established security and privacy engineering standards and on functional design requirements contributed by architecture and subsystem design tasks.
- Consortium details: 1 University and 1 Industry Partner
A Demonstrator for TPM-based Network Access Control
- Project duration: September 1, 2007 - December 31, 2008 (joint project April 1, 2008)
- Funding scheme: Commissioned research
- Project description: The project consisted of two parts: The first work package aimed on the elaboration and implementation of the protocol parts needed for Device Authentication (setup of a secure TLS tunnel based on keying material protected by the TPM and the proof of the TPMs validity) and User Authentication. Resulting in a demonstrator protocol for device authentication and user authentication. The second work package focused on the demonstrator protocol part performing the Remote Attestation of the device will be elaborated and implemented.
- Consortium details: 1 University and 1 Industry Partner
Authentication and Access Control using Trusted Computing Systems
- Project duration: January 1, 2008 - December 31, 2008 (joint project April 1, 2008)
- Funding scheme: Commissioned research
- Project description: The project consisted of two parts: The first work package WP1 aimed at investigating an end system (laptop) with Trusted Computing hardware for providing a secure and trustworthy platform without the need for a smart card (e.g. SIM card). An analysis of different TPM based boot concepts, namely Trusted Boot and Secure Boot was done. WP1 consisted of the following technical work items: (1) Analyse boot concepts for Trusted Computing End System (Trusted Boot with Remote Attestation, Secure Boot, RIM certificates) and (2) define client specific secure boot concepts for an infrastructure for secure boot or trusted boot on the device side. Second work package WP2 investigated an alternative means for user and device authentication, comparable to the functionality existing SIM cards. It aimed for describing a suitable functionality for authentication and access control (AA) and the interactions with the client platform of first work package. WP2 consisted of the following work items: (1) Functional architecture and (2) authentication and access control concept.
- Consortium details: 1 University and 1 Industry Partner
Sensor Wireless Application Network
- Project duration: September 1, 2009 - November 30, 2009
- Funding scheme: Commissioned research
- Project description: The project's investigations is splitted into two parts. The first part deals with the analysis of application scenarios corresponding possible attacks and blockades for wireless communication in a cabin of air plains. The state-of-art of security in Wireless (Sensor) Networks was analyzed followed by an analysis of selective application scenarios in a cabin corresponding possible impacts of data security. In the second part a definition of requirements for communication security in upcoming wireless communication architecture in a cabin is developed.
- Consortium details: 1 University and 1 Industry Partner
Self-Organized Data Acquision (SODA)
- Project duration: January 1, 2010 - December 31, 2011
- Funding scheme: BMBF Initiative KMU-innovativ: Informations- und Kommunikationstechnologie, No. 01|S09040C
- Project description: The aim of the project applied for here is the exemplary application of novel self-organization procedures from the field of radio-based distributed systems for data acquisition during crash tests in the automotive industry. The partners of the joint project expect the cooperation to provide information on whether wireless, self-organizing systems can meet the high demands on reliability and accuracy in this environment. On the one hand, the concrete basis is to be laid for a new generation of data acquisition systems for crash tests. On the other hand, the partners hope to gain general insights into the possibilities and limitations of wireless, self-organizing systems. These findings should pave the way for the use of the technology developed here in other application areas, such as mechanical engineering and automation technology.
- Consortium details: 1 University, and 1 Industry Partner
Smart Infrastructures for Smart Buildings (SI)
- Project duration: September 1, 2007 - ongoing (member April 1, 2008 - February 28, 2013)
- Funding scheme: Commissioned research
- Project description: The projects ambience is getting more enriched by technical equipment that aims to support us in our daily activities. In our homes these devices are motion detectors that turn on the light or start playing our favorite tune when we enter, microchips that control heating systems, Internet enabled TV sets and set-top boxes or remote controls for various devices and functions. The support that all these devices provide to residents in their daily lives can be enhanced by facilitating cooperation between. An intelligent home network that has access to all entities in a house might optimize energy efficiency (by demand driven heating), increase safety & Security (by presence control of e.g. iron and stove and by automatic door/windows locking mechanisms) and enhance comfort by adapting to user needs and habits. One of the major objectives is to provide autonomic mechanisms to integrate new devices into home networks. The project's focus is not only on enabling devices to participate at the cooperative but also to autonomously optimize the connected nodes all the time.
- Consortium details: 1 University and 1 Industry Partner
@ Fraunhofer Institute for Interfacial Engineering and Biotechnology, Stuttgart, Germany

Multi-Conditional Hybridization Intensity Processing System (M-CHiPS)
- Project duration: 2005 - 2016 (member April 2007 - March 2008)
- Funding scheme: Research project at the DKFZ Heidelberg, Heidelberg, Germany
- Project description: A data warehousing concept, focuses on providing both structure and algorithms suitable for statistical analysis of a microarray database's entire contents including the experiment annotations. It addresses the rapid growth of the amount of hybridization data, more detailed experimental descriptions, and new kinds of experiments in the future. We have developed a storage concept, a particular instance of which is an organism-specific database. Although these databases may contain different ontologies of experiment annotations, they share the same structure and therefore can be accessed by the very same statistical algorithms.
- Consortium details: 2 Research Institutes
