Future IoT ecosystems demand secure, privacy-aware multi-domain operation (MDO) across heterogeneous networks and stakeholders.
Since the late 1970s, when interconnected research networks laid the foundation for today's Internet, the primary goals were knowledge exchange and shared computational resources across institutional boundaries. Over the decades, affordable devices, ubiquitous connectivity, and large-scale digital infrastructures have driven a paradigm shift toward the Internet of Things (IoT), where billions of heterogeneous devices continuously communicate across domains. While foundational Internet technologies remain in use, they require substantial adaptation to meet emerging communication patterns, dynamic trust relationships, and stringent privacy expectations. As digitalization, automation, and continuous connectivity expand, privacy has become a core societal concern: the ability to control information disclosure directly influences liberty, innovation, and trust in digital ecosystems. Consequently, modern solutions must provide adaptable, reusable, and stakeholder-centric mechanisms for security, privacy, and trust—particularly in complex MDO scenarios.
Today, individuals commonly operate several IoT-enabled devices-ranging from smartphones and wearables to access credentials and smart infrastructure components. These devices differ in resources, communication technologies, timing constraints, and security capabilities. They interact through diverse communication patterns, including Human-to-Machine (H2M) and Machine-to-Human (M2H), Machine-to-Data-Lake (M2D) and Machine-to-Analytics (M2A), as well as Machine-to-Process (M2P) and Machine-to-Machine (M2M). In multi-domain environments - where devices, services, and stakeholders span organizational, administrative, and regulatory boundaries - these interaction patterns significantly increase complexity. Trust establishment, identity management, access control, policy enforcement, and secure data lifecycle management must function seamlessly across domains without sacrificing autonomy or compliance.
Thus, SeCoSys - Secure Communication Systems - addresses these challenges by investigating secure air/ground communications and broader IoT infrastructures under a unified multi-domain perspective. The work is structured along two interdependent pillars: Communication Networks and Data Management. The first pillar (blue) focuses on resilient architectures, secure transmission protocols, authentication and key management mechanisms, and cross-domain interoperability. The second pillar (orange) addresses privacy-aware data handling, access governance, secure storage, analytics integration, and compliance with evolving legal frameworks. Both pillars are systematically structured and interconnected through a set of overarching horizontal services, where these cross-cutting layers span all architectural components and ensure consistent operation across domains:
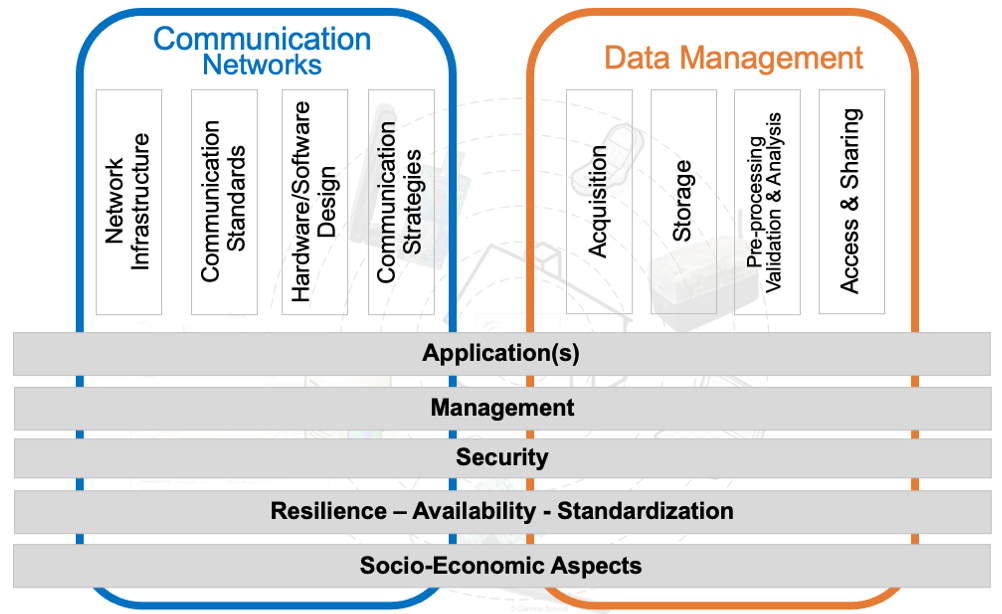
- Applications provide the functional integration of network and data capabilities into domain-specific use cases.
- Management enables orchestration, configuration, monitoring, and lifecycle control of distributed systems.
- Security establishes identity and trust management, access control, and protection mechanisms for communication and data handling.
- Resilience, availability, and standardization ensure interoperability, robustness, and continuity of operations across heterogeneous and federated environments.
- Socio-economic analysis evaluates regulatory compliance, stakeholder requirements, risk, and sustainability aspects.
Together, these horizontal services ensure that security, privacy, trust, and operational consistency are enforced coherently across both pillars and throughout complex multi-domain ecosystems.
Check also my homepage at University of Bundeswehr Munich under SeCoSys.
Area 1: Constrained Networks

Future IoT and CPS ecosystems require secure multi-domain operation (MDO) support as a foundational capability. Modern IoT and Cyber-Physical Systems (CPS) increasingly consist of heterogeneous, resource-constrained devices that interact across organizational, administrative, and technical boundaries. Research in this area address this evolution by systematically analyzing existing IoT platforms and their stakeholder ecosystems to identify requirements for secure communication, privacy preservation, and trust management in constrained environments - particularly in very constrained networks like Wireless Sensor Networks (WSN). These investigations revealed that stakeholders are not limited to device owners or operators, but include private end-users (e.g., individuals, residents, employees, caretakers) as well as public actors (e.g., identity providers, eService providers, governmental authorities), each posing distinct technical, legal, and ethical requirements such as anonymity, transparency, Privacy-by-Design, compliant data storage, and accountable service provisioning.
The existing SecureWSN framework provides a comprehensive, trustworthy security and privacy architecture tailored to constrained devices in Smart Home and Smart Building scenarios, supporting both active and passive components. However, SecureWSN currently represents a specialized case within a broader and more pressing research challenge: enabling secure and trustworthy MDOs. Future IoT and Industry 4.0 ecosystems demand federated solutions where multiple administrative domains - potentially spanning companies, public authorities, and private households - interoperate seamlessly while maintaining autonomy, regulatory compliance, and enforceable trust relationships. Addressing this requires scalable identity and access management, interoperable trust models, lightweight yet robust cryptographic mechanisms, and cross-domain policy enforcement suitable for constrained nodes. Consequently, current research extends SecureWSN toward a generalized MDO architecture, positioning constrained networks as a secure, privacy-aware, and regulation-compliant foundation for federated IoT and CPS deployments.
For more details check out the SecureWSN project page and click here.
For publications click here.
Area 2: Secure Aeronautic Communication

Connected aviation systems require secure communication and resilient decision-making across safety-critical IoT domains. Modern aviation systems - including aircraft and drones - have become an integral part of the Internet of Things (IoT). Aircraft and Unoccupied Aerial Vehicles (UAV) are increasingly connected to digital infrastructures to receive system updates, obtain navigation data, exchange operational information, and integrate into collaborative airspace management systems. While this connectivity enables efficiency, automation, and new mobility services, it also expands the attack surface and exposes safety-critical systems to cyber threats and misuse. Consequently, robust secure communication mechanisms and resilient, fast decision-making procedures are essential to ensure both operational continuity and immediate reaction capabilities in emergency situations.
Our current research in this domain is conducted in close cooperation with the German Aerospace Center (DLR) and Airbus Defence and Space GmbH, focusing on the intersection of safety, security, and connectivity in aeronautical environments. Current investigations address mutual authentication and key agreement mechanisms for the L-band Digital Aeronautical Communication System (LDACS), aiming to secure next-generation digital ground-based aeronautical communications. In parallel, research contributes to Air Mobility Integration (AMI) and Urban-Space concepts, enabling the safe integration of UAVs into controlled and uncontrolled airspace while ensuring trustworthy coordination between multiple stakeholders and domains. Furthermore, safety and security aspects of UAV operations are examined holistically, recognizing that cyber incidents in aviation are inherently safety-critical and demand tightly coupled security-by-design and safety-by-design approaches.
Overall, this research positions connected aviation systems as a safety-critical extension of the IoT, where secure authentication, resilient communication architectures, and real-time response capabilities are fundamental prerequisites for trustworthy air mobility and future autonomous flight ecosystems.
For more details check out the Aeronautical project page and click here.
For publications click here.
Area 3: Socio-Economic Investigations
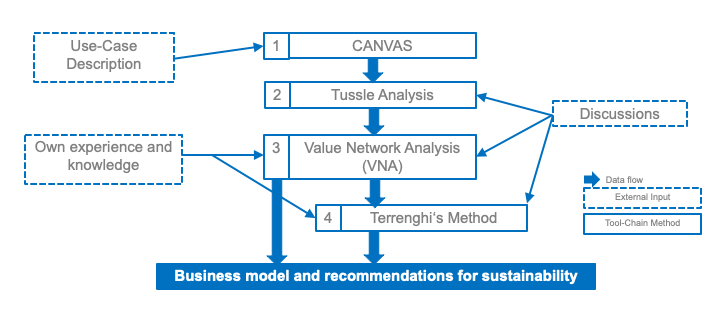
Any development of technologie (independent if software or hardware) requires acceptence by the final end-users, which highly influence the success on the targeted market. Thus, it is essential to understand (1) the current market, (2) the different stakeholder groups including their needs and wishes, (3) the required investigations, and (4) the expected influences to existing technologie. With this knowledge in place an individual business model and recommendations for sustainability can be defined.
Therefore, it is recommended to apply our developed 4-step tool chain combining well-accepted methods (e.g., CANVAS and Value-Network-Analysis) with newer methods (e.g., tussle analysis and Terrenghi's method) in order to define a proper business modell and sustainability recommendation. It requires a well-defined scenario as initial input. Further input can include individual experiences and detailed technical knowledge. Each step creates specific output that can be used on its own for the individual purpose of the method applied. Within the approach proposed here the output is in return used as input for the next step of the method. Additionally, discussions between developers and target customers need to be included in the process of the tool-chain in order to receive feedback for each step of the process.
This tool-chain is partly standardized by the ITU and was applied for several use-cases within the project symbIoTe.
For publications click here.

